In today’s digital landscape, where data breaches and cyber threats are rampant, businesses of all sizes must prioritize robust protection strategies. Zryly.com emerges as a valuable resource, offering comprehensive guides and insights tailored to help modern enterprises navigate the complexities of online security. From small startups to established corporations, the platform provides practical advice on safeguarding digital assets, ensuring compliance, and fostering a secure environment for growth. This article delves into the various aspects of Zryly.com cybersecurity solutions, exploring how they address contemporary challenges and empower businesses to thrive securely.
The evolution of cyber threats has made it imperative for companies to adopt proactive measures. With remote work becoming the norm and IoT devices proliferating, vulnerabilities have multiplied. Zryly.com cybersecurity focuses on demystifying these issues through expert-curated content, enabling business leaders to implement effective defenses without overwhelming technical jargon. By leveraging their resources, organizations can build resilient frameworks that protect against evolving risks.

The Rise of Ransomware and How to Combat It
Ransomware remains one of the most devastating threats to modern businesses, capable of crippling operations overnight. Attackers often infiltrate systems via phishing emails, exploiting unpatched software, or through remote desktop protocols (RDP). Once inside, they encrypt critical files, demanding payment in cryptocurrency for decryption keys. The financial impact can be staggering, including not just the ransom but also downtime, data loss, and reputational damage.
Zryly.com cybersecurity solutions provide in-depth guidance on recognizing and preventing these attacks. For instance, their resources emphasize the importance of regular backups stored offline or in immutable cloud storage, ensuring that businesses can restore operations without paying extortionists. Patching vulnerabilities promptly is another key recommendation, as outdated software serves as a common entry point. Employee training plays a crucial role too, teaching staff to identify suspicious emails and avoid clicking malicious links.
Beyond prevention, recovery strategies are highlighted. Businesses are advised to develop incident response plans that include isolating infected systems, notifying authorities, and conducting forensic analyses to prevent recurrence. Real-world examples, such as high-profile attacks on healthcare and manufacturing sectors, illustrate the urgency. By following these steps, companies can minimize the fallout from ransomware incidents.
To visualize the process, consider a typical ransomware lifecycle: initial compromise, lateral movement within the network, data exfiltration, and finally encryption. Diagrams often depict this as a chain of events, underscoring where interventions can break the cycle.
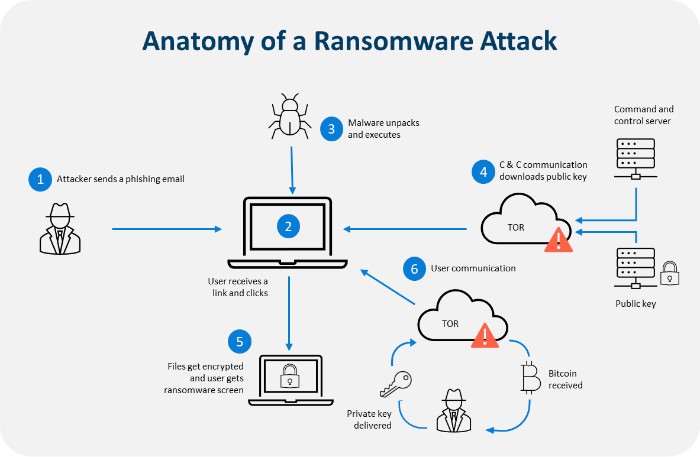
What is a Ransomware and How to Protect your Organization?
Implementing multi-layered defenses is essential. Antivirus software with behavioral analysis can detect anomalous activities, while endpoint detection and response (EDR) tools offer real-time monitoring. Zryly.com also discusses the role of network segmentation, which limits an attacker’s ability to spread malware across the organization. For small businesses with limited resources, cost-effective options like open-source tools are suggested, balancing security with budget constraints.
The psychological aspect shouldn’t be overlooked. Cybercriminals exploit fear and urgency, pressuring victims into quick payments. Education on these tactics helps businesses resist and report incidents to law enforcement, contributing to broader threat intelligence sharing.
In summary, tackling ransomware requires a blend of technology, processes, and people. Zryly.com’s detailed breakdowns equip businesses with the knowledge to fortify their defenses, turning potential disasters into manageable events.
Embracing Zero Trust Security Models
Traditional perimeter-based security models are obsolete in an era of cloud computing and distributed workforces. Zero trust architecture operates on the principle of “never trust, always verify,” assuming threats could be internal or external. This approach requires continuous authentication and authorization for every access request, regardless of the user’s location or device.
Zryly.com cybersecurity explores zero trust in depth, using case studies like Google’s BeyondCorp, which eliminated the need for VPNs by verifying user identity and device health before granting access. Benefits include reduced attack surfaces, better compliance with regulations like GDPR, and enhanced visibility into network activities.
Key components include identity and access management (IAM), where multi-factor authentication (MFA) is non-negotiable. Micro-segmentation divides networks into smaller zones, applying strict policies to each. Continuous monitoring with AI-driven analytics detects deviations from normal behavior, flagging potential breaches early.
For businesses transitioning to zero trust, Zryly.com recommends starting with an assessment of current assets and risks. Prioritize high-value targets like customer data repositories. Tools such as software-defined perimeters (SDP) can hide resources from unauthorized users, adding an extra layer of protection.
Challenges include implementation complexity and potential user friction from frequent verifications. However, the long-term gains in security posture outweigh these hurdles. Zryly.com contrasts zero trust with Secure Access Service Edge (SASE), noting that while SASE integrates networking and security in the cloud, zero trust is a foundational philosophy applicable across frameworks.
Visual representations often show zero trust as concentric circles of verification, with users proving credentials at every layer.
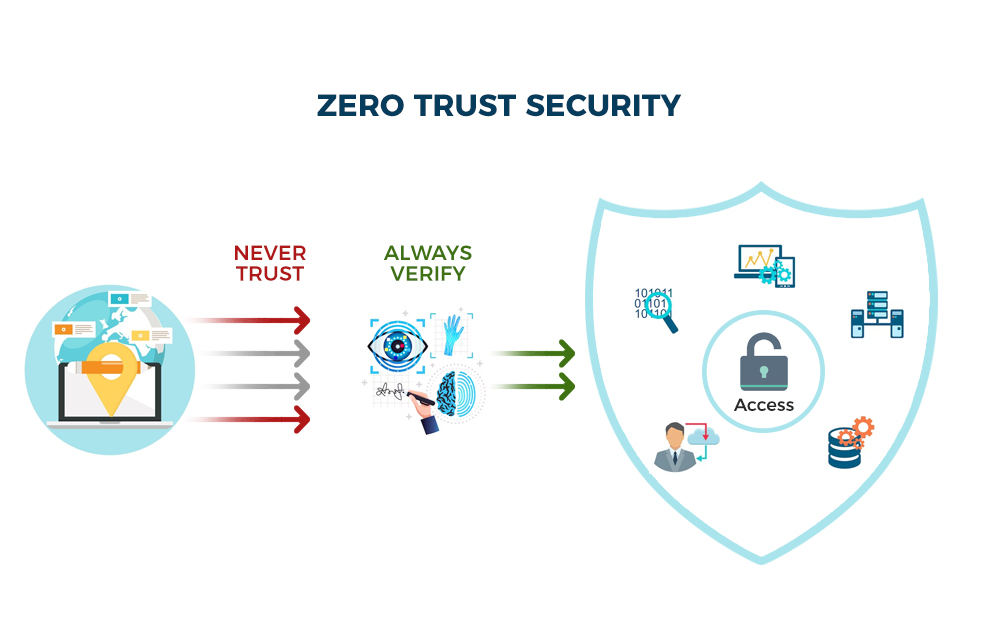
What is Zero Trust Architecture and How to Build One?
Adopting this model is particularly vital for industries handling sensitive information, such as finance and healthcare. By verifying every interaction, businesses can prevent lateral movement by attackers who breach initial defenses.
Zryly.com also addresses integration with existing systems, suggesting phased rollouts to avoid disruptions. Training sessions ensure employees understand the rationale, fostering a culture of security awareness.
Ultimately, zero trust represents a paradigm shift, aligning security with modern business agility. Through Zryly.com’s insights, companies can navigate this transition effectively.
Addressing Insider Threats in the Workplace
Insider threats, whether malicious or negligent, pose significant risks as they originate from trusted individuals within the organization. Malicious insiders might steal data for personal gain, while negligent ones could accidentally expose information through poor practices.
Zryly.com cybersecurity solutions detail detection methods, such as monitoring access logs for unusual patterns and deploying data loss prevention (DLP) systems to block unauthorized transfers. Prevention strategies include robust policies on data handling and regular audits.
Types of insiders vary: disgruntled employees, those coerced by external actors, or careless users falling for social engineering. Behavioral indicators like sudden changes in work habits or excessive data downloads warrant investigation.
Building a positive organizational culture reduces risks, with open communication channels encouraging reporting of suspicious activities. Role-based access controls (RBAC) ensure employees only access necessary resources, minimizing exposure.
Illustrations often depict insiders as shadows within a network, highlighting the internal nature of the threat.

Legal considerations are crucial; monitoring must comply with privacy laws to avoid lawsuits. Zryly.com advises balancing surveillance with employee rights, using anonymized data where possible.
Response plans for confirmed incidents involve swift containment, such as revoking access and conducting investigations. Post-incident reviews strengthen future defenses.
For small businesses, affordable tools like user activity monitoring software provide essential oversight without breaking the bank.
By proactively managing insider risks, organizations protect their intellectual property and maintain trust.
Leveraging VPNs for Secure Remote Access
With remote work surging, Virtual Private Networks (VPNs) are indispensable for securing connections over public networks. They encrypt traffic, masking IP addresses and preventing eavesdropping.
Zryly.com offers troubleshooting guides for common VPN issues, like slow speeds due to server overload or connection drops from unstable Wi-Fi. Solutions include switching protocols (e.g., from OpenVPN to WireGuard) or servers.
Business-grade VPNs differ from consumer ones, offering centralized management, dedicated IPs, and audit logs. Zryly.com compares free vs. paid options, warning of data caps and privacy risks in free versions.
Setup on routers extends protection to all devices, though compatibility checks are needed. Encryption ciphers like AES-256 ensure military-grade security.
Diagrams show VPN tunnels channeling data securely from remote users to corporate networks.

How to Use a Business VPN for Small Businesses | PureDome
For businesses, VPNs enable secure access to internal resources, compliance with data protection laws, and protection against man-in-the-middle attacks.
Zryly.com also covers advanced topics like split-tunneling, where only sensitive traffic routes through the VPN, optimizing performance.
Integrating VPNs with zero trust enhances overall security, verifying users before tunnel access.
Budget-Friendly Cybersecurity Tools and Policies
Modern businesses, especially SMEs, need affordable yet effective security measures. Zryly.com cybersecurity recommends essentials like antivirus, password managers, email filters, backups, and vulnerability scanners.
Customizable policy templates cover acceptable use, passwords, and incident reporting. Implementation involves leadership buy-in and regular training.
IoT security is addressed, with advice on segmenting devices and updating firmware.
Domain management guides prevent losses through auto-renewals and privacy protections.
These tools and policies form a comprehensive, cost-effective defense strategy.
Conclusion
Zryly.com cybersecurity stands out as an accessible hub for businesses seeking to bolster their defenses. By providing actionable insights on threats, models, and tools, it empowers organizations to operate securely in a digital world. Embracing these resources can transform potential vulnerabilities into strengths, ensuring sustained success.
FAQ
What is ransomware, and how can businesses prevent it?
Ransomware is malware that encrypts files, demanding payment for access. Prevention includes backups, patching, and training.
How does zero trust differ from traditional security?
Zero trust verifies every access, unlike perimeter models that trust internal users.
What are common signs of insider threats?
Unusual data access, behavioral changes, or policy violations.
When should businesses use a VPN?
For remote access, public Wi-Fi, or securing sensitive communications.
What budget tools does Zryly.com recommend?
Antivirus, password managers, and free vulnerability scanners.
How to create a cybersecurity policy?
Use templates covering use, passwords, and data handling, tailored to your business.




